IBM Sterling Secure Proxy
Helps shield your trusted network by preventing direct connectivity between external partners and internal servers.
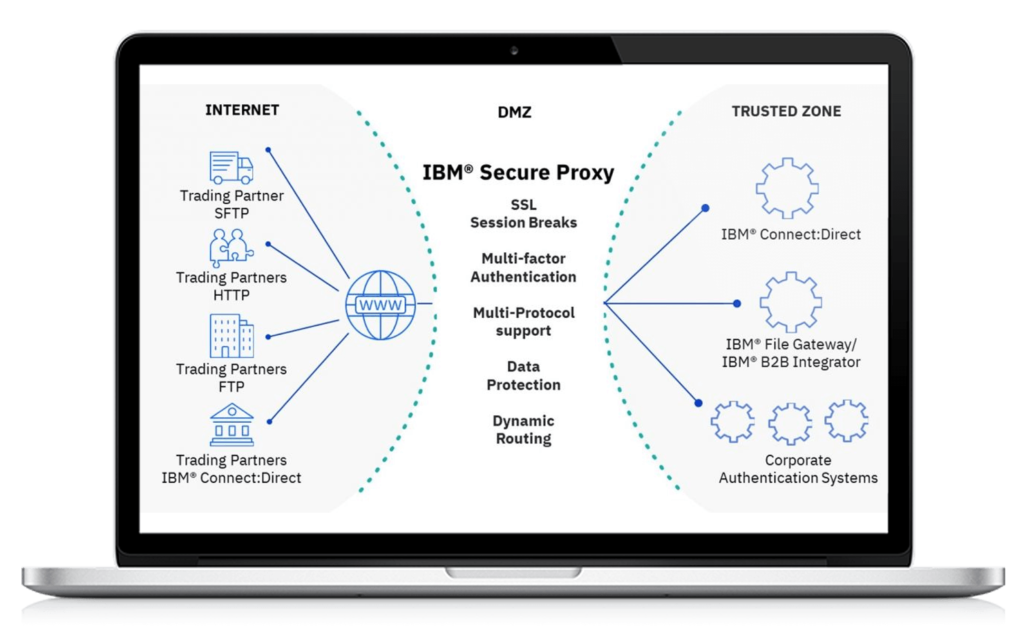
IBM Sterling Secure Proxy - SSP
Pragma Edge’s IBM Sterling Secure Proxy (SSP) helps shield your trusted network by preventing direct connectivity between external partners and internal servers. It can secure your network and data exchanges at the network edge to enable trusted business-to-business transactions and Managed file transfer (MFT) file exchanges. As a demilitarized zone (DMZ)-based proxy, Sterling Secure Proxy uses multi-factor authentication, SSL session breaks, the closing of inbound firewall holes, protocol inspection, and other controls to ensure the security of your trusted zone.
IBM Sterling Secure Proxy is a DMZ-based application software proxy enabling secure and high-speed data movement over the internet. It provides increased perimeter security to protect the enterprise’s trusted zone, as well as authentication services to prevent unauthorized access to your business-critical internal systems. It integrates with your existing security infrastructure to meet security and audit requirements while also supporting compliance regulations and incorporating industry standards and best practices.
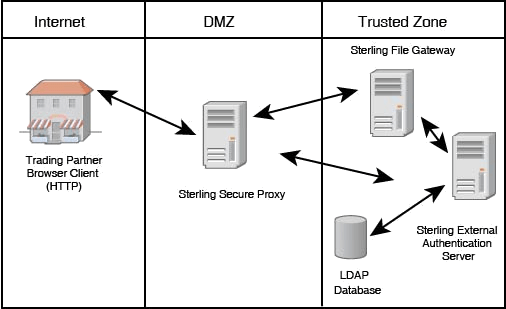
Enable Trusted Transactions
Pragma Edge’s IBM Sterling Secure Proxy (SSP) secures and shields your trusted network by preventing direct connectivity between external partners and your critical internal servers. Partner connections for B2B transactions and MFT file exchanges are intercepted at the edge and following authorization are transparently redirected to trusted connections within your enterprise.
Enable Speed and Transparency
IBM Secure Proxy offers a bridging capability for a high-speed protocol to the mainframe to support the IBM Connect: Direct High-Speed add-on option (HSAO). HSAO enables speedy and efficient transfers of large files over long distances. This also brings transparency to your migration projects.
Governance and Compliance
A fully IBM Watson Supply Chain Data Sheet integrated interface to external ID stores eliminates the need for duplicate stores and local accounts, providing a single source for user and partner credentials. Interfaces to HSMs support the use of these devices for key storage.
Operational Management
Multiple Secure Proxy engines may be deployed in the DMZ for traffic separation, load balancing, and capacity management. A Configuration Manager console is provided for the creation and management of all proxy configuration objects and for managing the proxy engine(s) in the DMZ. The configuration is always performed inside the trusted zone to ensure the protection of configuration and management activities.
IBM Sterling Secure Proxy - SSP Services Includes:
Deliver high secure B2B and MFT solution utilizing the IBM Sterling Secure Proxy.
Deliver Context based routing.
Set up high availability and Disaster recover with IBM Sterling Secure proxy.
Integrate authentication of FTP, FTPS, SFTP and AS2 protocols with LDAP or Active Directory for authentication.
Build SSO with B2B, MFT and Portal solutions.
Develop SSL session breaks and multi-factor authentication.
Providing support for managing engines, Adapters.
Build High-availability and load-balanced clustered environments to ensure business continuity and optimal performance.
IBM Connect Enterprise context based routing.
Sterling Secure Proxy (SSP) Service - FAQ's
Sterling Secure Proxy acts like a firewall between partners and the organization’s internal servers. Generally, SSP is deployed in DMZ.
Initially, users from the internet will be first routed to the SSP, which is present in DMZ and from that, only the trusted users are routed to the application like SI, which is present in a private zone.
DMZ allows the user from untrusted networks like the internet to access the application, which is present in a private network.
- Trusted transactions: Using SSP, the trusted user can access the application and make file transactions
- Speed: Using SSP, we can make transactions secure while not reducing the response time of the application
- SSP: can also act as a load balancer while diverting the users from the public network(internet) to the application present in the private network.
- SSP supports: multi-factor authentication and allows users to use different protocols while making file transactions
Netmap is used to establish a connection securely, we will hide the actual port of our server adapter, and we will give another port that is configured in ssp netmap with this client will not be able to establish the connection directly.
For example, we have created an adapter with port no 24. We will not provide 24 ports to the client, and we will create another port like 21 and configure in netmap with inbound and outbound rules, and we will give 21 ports to a client; he will establish a connection with 21 port and it will route to 24 ports in ssp, our actual server port in SI.
Inbound and Outbound rules are used for authentication. In this, we will give ip addresses of our servers. In inbound, we will give the client IP so that it will cross-check the ip and establish a connection; otherwise connection will not establish In outbound, we will give the server IP so that the client ip connection will route to the server and establish the connection between the client and server
YES, we need to add every ip of clients to establish a connection or otherwise we have one option to allow all IP’s that is in place of ip if we give *
it will allow all IP’s from that particular connection
YES, we have user authentication also we can give a particular user name who wants to establish a connection, we can add this to policies
IBM Sterling Secure Proxy helps shield your trusted network by preventing direct connectivity between external partners and internal servers. It can secure your network and data exchanges at the network edge to enable trusted business-to-business transactions and managed file transfer (MFT) file exchanges.
Sterling Secure Proxy Engine—the engine resides in the DMZ and contains the minimum components necessary to manage communications sessions. The engine configuration (Sterling Secure Proxy engine properties) is created at Configuration Manager and pushed to the engine.
1. Place a server that is meant for public access in a network that is separate from your local or internal network.
2. Disable utilities that allow remote users to access the server’s internal processes.
3. Use packet filtering and firewalls.
4. Control CGI scripts.
2. Disable utilities that allow remote users to access the server’s internal processes.
3. Use packet filtering and firewalls.
4. Control CGI scripts.
Proxy servers act as a firewall and web filter, provide shared network connections, and cache data to speed up common requests. A good proxy server keeps users and the internal network protected from the bad stuff that lives out in the wild internet. Lastly, proxy servers can provide a high level of privacy.


