
IBM watsonx for Enterprise Asset Management
IBM watsonx for Enterprise Asset Management: Leveraging AI to Boost Efficiency and Performance Enterprise Asset Management (EAM) is undergoing a significant transformation,
Logging is an essential aspect of information security. It provides a clear history of what happened in the network and on the different assets. It helps you to understand the threats, their nature, time, and other details.
This is a guide to implementing a security log management system to help you defend and secure your network.
Security logging is a process of collecting and recording events that have been generated throughout the IT infrastructure and providing access control to this data. Security logs can be used to monitor the security of the network and its components and the activity of users and applications.
They provide the raw network activity data and are the first place to look when a networking event occurs. Security logs are typically stored in a log monitoring, and management application and are stored in a structured format for easy searching and analysis. Often, logs are imported into a SIEM (Security Information and Event Management) system for further analysis and reporting.
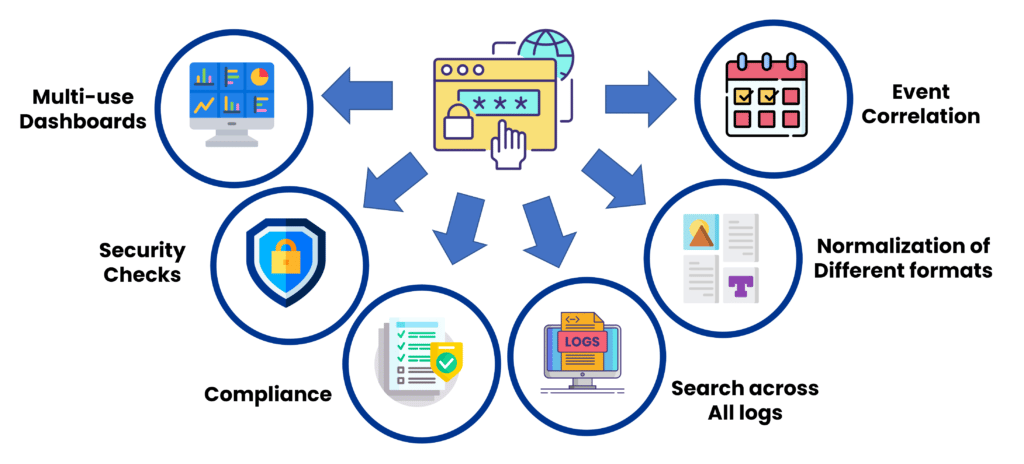
If you’re looking for the best ways to manage and log security information, look no further than our list of best practices. We’ll show you how to use logs to improve your security posture effectively.
You may have a solid security strategy in place, but your team needs to know what’s expected of them to succeed. Doing this can prevent unauthorized changes from occurring within your company and ensure everyone understands the importance of data security.
Defining your goals and objectives will help you better organize your strategy and security measures, and it’ll also help you identify any potentially vulnerable areas of your current security plan.
Security logs are the lifeblood of any security information. They contain key data to help you manage your application, troubleshoot issues, and identify security threats. However, some logs are more important than others.
Be aware of what to log or what not to. It’s optional to track everything just because you can; collecting too much data might make it more difficult to retrieve important information. Additionally, having more logs to maintain makes your log maintenance and storage operations more difficult.
Calculating the storage capacity for security logs should consider significant load peaks. When systems function well, the daily data generation is almost consistent and determined mainly by the system usage and daily transaction volume. We often observe an increased log output rise when serious system problems occur.
The most recent logs, which are necessary for repairing system faults, are lost if the log file reaches its storage limitations. The storage system of the security log must function as a circular loop that removes the previous data once imposing a storage limit.
Logs can be used to analyze various metrics such as response time, connections, or even the amount of data transferred. It is like having a complete track of your website and its performance. Logs can also be used to detect an issue in your website that may be causing a security breach or a problem with your website.
For example, if you find many connections from a single source to your website, there might be a security breach from a bot or virus trying to scan or attack your website. This is just one way that logs can help you keep your website secured. To improve the security of your network, you must have a reliable solution for log management.
Logs include private information. A security log policy should examine confidential material, such as customer personal information or internal API access credentials. Before sending log data to any third-party provider, make extra sure to encrypt any private information.
Security Logs are a critical component of any Information Security Program. They can be used for various purposes, but at their core, logs are a record of events, whether they are malicious or benign. A security log analyzer is a tool that performs pattern matching on varying formats of logs, which can be tremendously time-consuming if performed manually.
There are several different security log analyser tools that are available today. A decent security log analyser will help you manage security logs better and make educated log monitoring decisions.
Security logs track application and network activity. Security log data is used to detect security events, assess threats, and understand what has happened. Despite the importance of security logs, many organizations need help to store and manage log data in a way that is cost-efficient and scalable.
It is challenging to handle security logs. A small business generally produces a lot of loggable data, even if it just records the events corresponding to the most crucial metrics. Large businesses can generate hundreds of terabytes of log data. It’s difficult to manage this steady data flow since it’s so large.
Logs need to be normalized since they originate from several endpoints and have diverse sources, formats, and formats. The goal is to organize the data consistently, making it simple to search, compare, and read. To share and keep records, systems, and files must be extremely secure, and accessibility must be strictly regulated. They must also be able to process massive volumes of data without affecting the entire system’s efficiency.
A log is an essential part of any security infrastructure. It helps the security team collect, report, and monitor the activity on the network. Logs help security analysts to detect, investigate and prevent security breaches. The Security Log also provides information needed to comply with regulatory requirements. As a result, logs should be enabled as soon as possible after the initial deployment of the network infrastructure.
Browse Categories
Share Blog Post

IBM watsonx for Enterprise Asset Management: Leveraging AI to Boost Efficiency and Performance Enterprise Asset Management (EAM) is undergoing a significant transformation,

Building a Connected Enterprise for Ingram Content Group What Our Clients Say “The Pragma Edge team’s collaboration and expertise were key to

IBM Sterling for Modern B2B Integration, EDI, and Managed File Transfer: A Practitioner’s Guide Introduction B2B integration today is more than just
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |
Thank you for submitting your details.
For more information, Download the PDF.
Thank you for registering for the conference ! Our team will confirm your registration shortly.
Invite and share the event with your colleagues
IBM Partner Engagement Manager Standard is the right solution
addressing the following business challenges
IBM Partner Engagement Manager Standard is the right solution
addressing the following business challenges
IBM Partner Engagement Manager Standard is the right solution
addressing the following business challenges